ATC Resources
Future-Proofing Recording Systems for Data Integrity in ATC
What should you look for in a future-proof recording system to ensure security and integrity of data, while maintaining user flexibility and ease of access?
In recent years ATC recording systems have taken on greater complexity to simplify data capture, management and playback for ATC installations and their staff. Where recording systems were once passive solutions that connected to the source data through isolated hardware interfaces, they are now fully integrated content management solutions with ranges of features tailored to each data type they capture. As they become more complex and more deeply entrenched in the systems and data they are designed to capture, a renewed focus on data integrity and security has emerged.
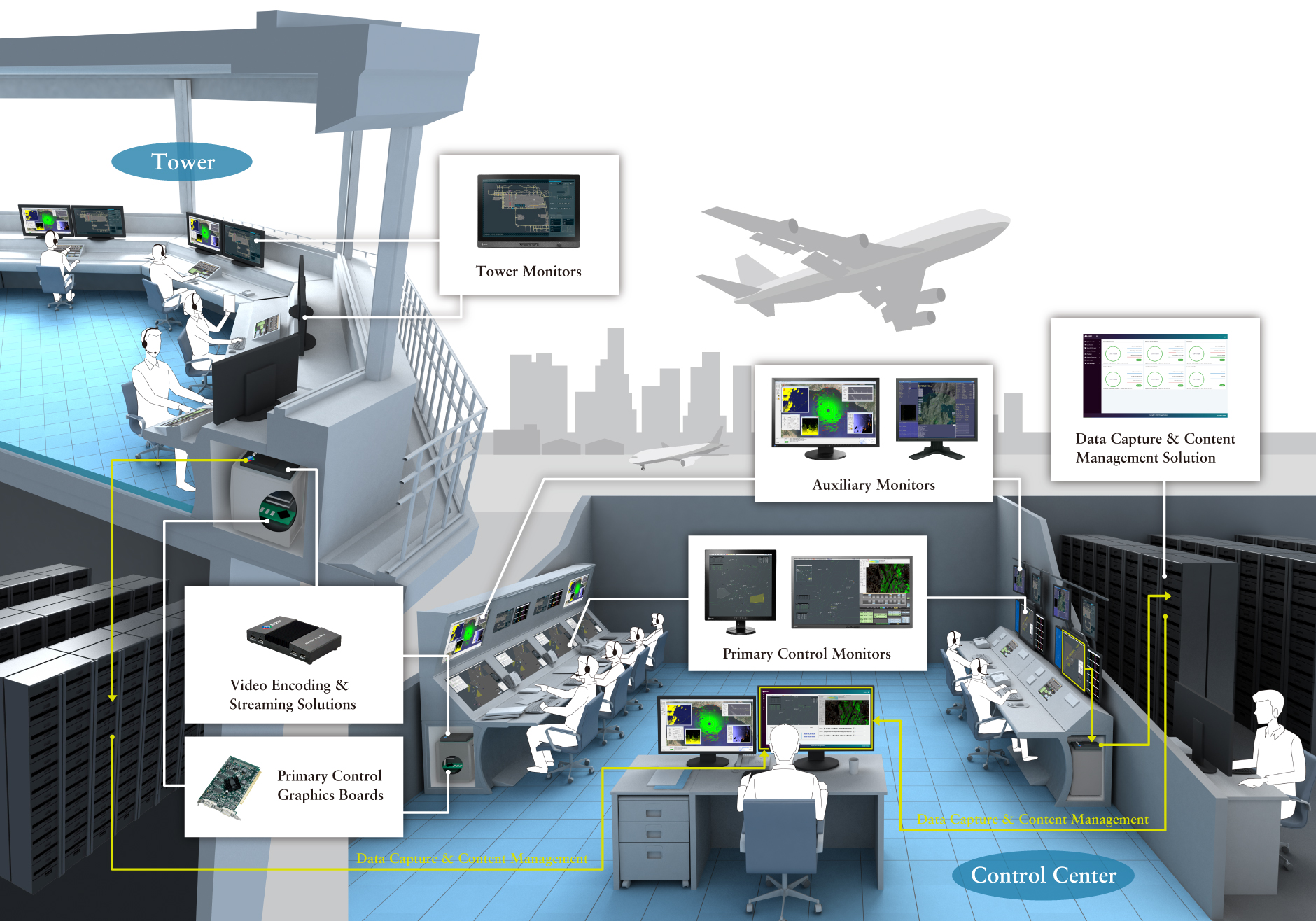
As more data sources use networking infrastructures, a range of communication and security challenges are exposed. Not only is the data itself at risk, but so is the system architecture of the data capture solution and its effect on operational systems. This is reinforced by, for instance, ED-137, the ‘Interoperability Standards for VoIP ATM Components’ and an emerging need for active voice over internet protocol (VoIP) recording in ATC facilities. With these new challenges there are many issues that ANSPs must face to minimize the risk of data breaches and other security problems when selecting a recording solution.
Modern data capture and content management solutions such as EIZO’s SafeGuard are built from the ground up to provide maximum flexibility and customizability while maintaining a highly secure environment. Given that internal ATC networks are carefully isolated from other networks, access from within a facility’s dedicated and shared WAN connections have become the main focus for solution providers.
Security is Paramount
Before considering the network, operating system (OS), and software-related security implications, it should be said that security and data integrity at a server hardware level is no less important. Physical security such as lockable cabinets or hard disk drive (HDD) bays should always be standard practice. In addition, guaranteed data integrity through the provision of fault-tolerant RAID storage systems, solid-state drives (SSD), dual power supplies (PSU) and ‘hot swap’ components (whereby a device is replaced by a similar device while the computer is still in operation) virtually guarantees 100% availability of the data held in a suitably well-designed system. Having checked those boxes, system architects can focus on the remainder of the solution.
In a typical IT system, there are several layers of security that should be considered. Only by addressing all such considerations will ANSPs be able to minimize the potential for data breaches or loss. For those ANSPs and other organizations without a dedicated staff of security experts, the fundamental aspects of the recording solution, OS, application layer, data format, encryption options, and data transfer methodology are key considerations in minimizing risk and limiting exposure to data loss. After physical hardware security, the second top priority is network security. If one simplifies the security of a typical system into layers or ‘gates’ that need to be passed through to access the data held within, a typical system could comprise a WAN and LAN, the capture server, the capture and playback application, and the data itself.
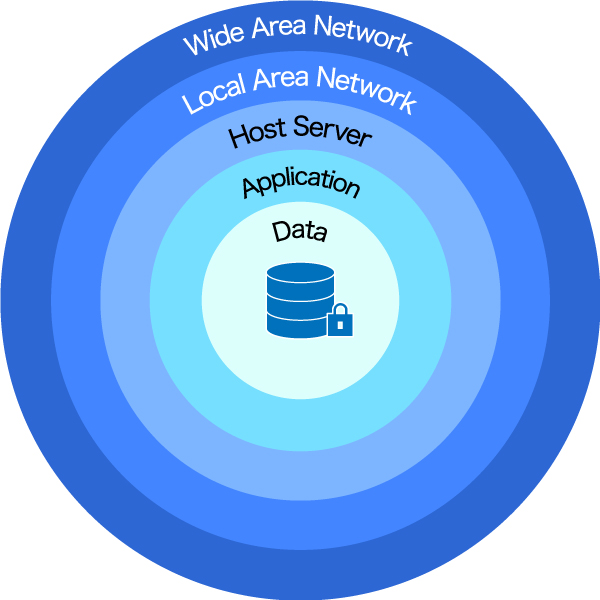
Typical IT security layers of an ATC recording system with the captured data stored locally on the capture server.
In a multisite solution the WAN would comprise multiple LANs at each site, linked through the network infrastructure. Traditionally, dedicated leased lines were used, but increasingly WANs are being implemented over the internet, using the same encryption technologies as virtual private networks (VPN), such as internet protocol security (IPSEC). Indeed, IPSEC and other encryption technologies can be used within a LAN to create an isolated virtual network on the same physical infrastructure. In such instances, firewalls and routers are used to establish the first layers of security and to protect against malicious attempts to access the LAN and its data at each site. For a single-site solution, the capture network could be isolated from other networks to provide further protection from any external attempts to access the data, or firewalls could be provided between the capture network and any other connected LAN. Firewalls are designed to stop malicious traffic and, if properly configured, will leave the capture server and application layers to provide further internal protection. Typically, routers and firewalls are the responsibility of the ANSP’s network infrastructure partner, telco or ISP.
Capture Server Considerations
For recording solution providers, the capture server is the principal component and will comprise software and hardware, with configurations designed to support the environment and data required to be recorded and retained. Typically, data capture and content management systems are built on top of industry standard server blade technology, using Intel or AMD server CPUs and enterprise-grade disk storage solutions.
In a secure ANSP facility, data breaches are unacceptable and as a fundamental element in the running of the data capture and content management software it is necessary to consider the most critical layer of the overall security solution – the OS. By selecting a Linux-based OS, an extensive range of powerful in-built security features becomes available. One such feature is security-enhanced Linux (SELinux), which is a kernel-level facility that can be used to grant highly specific access rights to users and processes, only allowing activities that are specifically enabled to be available.
Furthermore, Linux is open source. With a vast community of contributors and critics that focus heavily on security and stability, Linux has a very effective self-policing development model that benefits from massive-scale peer review. Formal testing procedures have emerged to proactively identify potential weaknesses, and when flaws are discovered the community acts to correct them with a speed and efficiency unmatched by any monolithic proprietary software vendor. As a result, modern security-hardened Linux has few rivals that approach this degree of robustness.
In addition, there are several security-focused Linux distributions, each with its own strengths. Unlike Windows, which is a monoculture, this variety makes security attacks far more difficult. The salient issue with a monoculture is that it is all vulnerable to the same attack. Solutions such as EIZO’s SafeGuard use a modern version of Linux on the data capture server component, with up-to-date protocols following the latest security standards. By designing the solution from the outset based on an enterprise-grade Linux distribution, such solutions benefit from the enhanced security and efficiency that Linux offers.
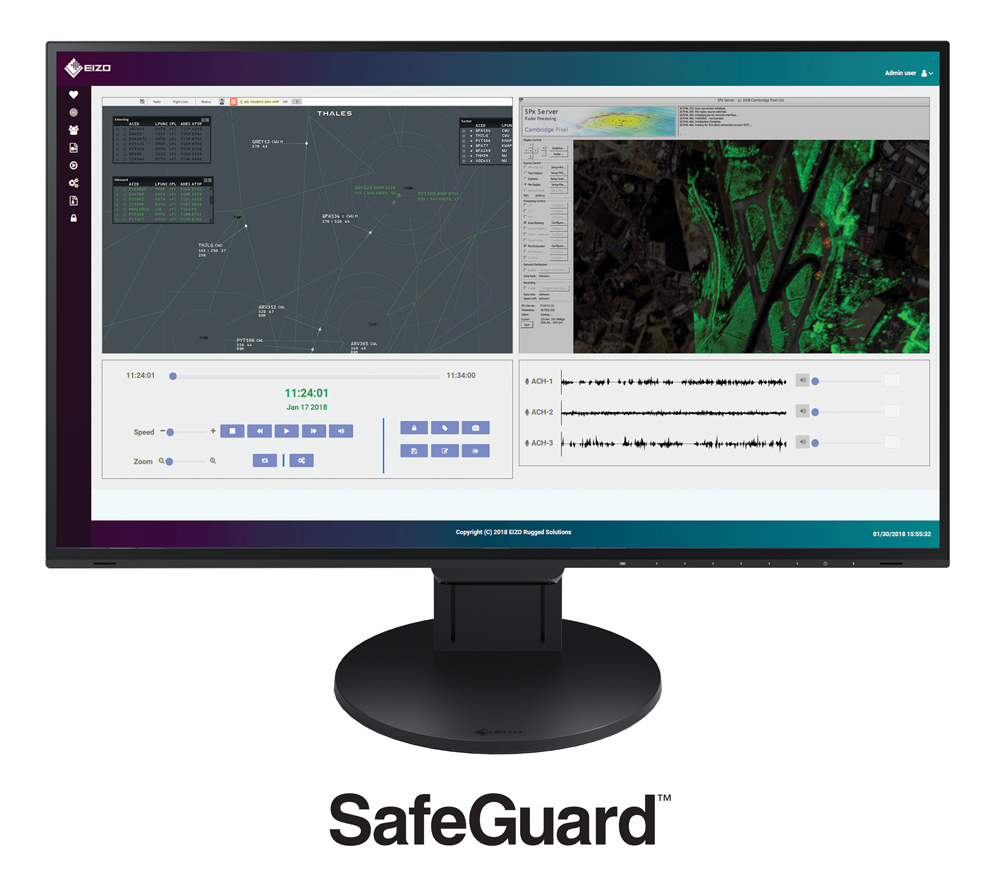
EIZO’s SafeGuard is a data capture & content management solution designed to receive multiple feeds from communication interfaces employed in mission-critical environments.
Docker, a computer program that performs OS-level virtualization – also known as containerization – allows the developer to put entire server subsystems into their own sandboxes, effectively isolating key facilities from each other and the underlying OS in their own virtual machine environment. In the highest security applications, where data is extremely sensitive, the ability to encrypt captured data should be available. Optionally files written to secondary or quarantine storage could also be encrypted. Options for data encryption should be considered and provided in accordance with the local relevant standards. For example, according to the appropriate US federal data protection standards, at least 128-bit keys or longer are required. Encryption of the captured data ensures that, in the event of data being removed from the system without using the integrated software tools and processes, it is unreadable.
Content Management
Once the target data is recorded, retained and held securely by the capture server, the need to access the recorded content becomes the next consideration. Whether the data is required to be reviewed immediately, or at some point in the future determined by the data retention capabilities of the system configuration, data access and the security of such access is of the utmost importance. The most secure systems do not allow direct access to the capture server itself but provide access through remote software clients on workstations via the network. This physical separation provides yet greater security to the overall system, meaning that the capture server can reside in an enclosed, secure environment.
Software clients used for data access can be ‘thick’ (for example an installed application) or ‘thin’ (using a web-based interface). Significant advantages of a web-based thin client solution include the ease by which multiple workstations can support the feature set without the need for software installation and the inherent secure communication methods built into modern web browsers. Furthermore, any future update process is restricted to the capture servers themselves, with additional features on the clients being automatically available to any connected client post update. This whole approach ensures that maintenance and administration is a simplified process and requires considerably less resource support.
Further advantages of a web-based approach include the ability to support a multiplatform environment. If the captured data is secured on a Linux-based server, using web-based access does not limit users to this OS for user access and management features. Additionally, browsers like Firefox and Chrome are also open source, benefiting from the same security-focused peer review as Linux. In support of this ideal, the SafeGuard solution provides a web-based user interface that employs proper authentication measures to ensure that all transactions between the web client and server are secure.
Multirole System Access and Playback
Any system, irrespective of its client configuration, should support the creation of unique user IDs and passwords with suitable privilege levels and auditing procedures to ensure that all user interaction is appropriately restricted and logged. Internal breaches can then be quickly and easily addressed through the inspection of audit logs, accessible by the administrator.
|
Today, playback solutions have the ability to transfer the data over the network on demand, in much the same way as modern audio and video streaming services. In systems such as SafeGuard, the capture server also acts as a media server, meaning that the data is not transferred as a complete file. Instead, only required packets of data are sent for the purposes of ad hoc playback on demand. This approach has shorter startup times than those that transfer whole files to the client, and it is more secure than traditional systems because less data must be transmitted to the playback workstation and no data is saved to the workstation’s local storage. Data never leaves the capture server as a complete file, unless required to do so by management functions such as export and copy. These functions can be protected and allowed only to users with the highest privileges, to further minimize the chances of files being removed from the system by unauthorized persons. |
In SafeGuard’s system, only required packets of data are sent for the purposes of ad hoc playback on demand. |
In summary, any data capture application should place special focus on security, using approaches like highly restricted file access, automatic logouts and timeouts, user accounts and permissions, auditing and logging, remote access management and host access management, to address potential security vulnerabilities at the application layer. Web-based clients like those implemented in EIZO’s SafeGuard solution lend themselves perfectly to this approach.
Proprietary Streaming Protocols
As the need develops for data to be held outside any subsystem, for example using cloud storage, the format of the data and its ease of access is important. While data can be encrypted post receipt by the capture server, data transmitted over a network before it reaches the capture server should also be secured. While proprietary protocols are sometimes seen as a limitation of a data encoder, in security critical applications they serve a dual purpose. Open standard encoding protocols means that the data can easily be reviewed using free software tools and applications with minimal effort, while proprietarily encoded data provides a further layer of security and barrier to data access. With proprietary encoding, only with the software tools provided can the data itself be decoded and reviewed.
|
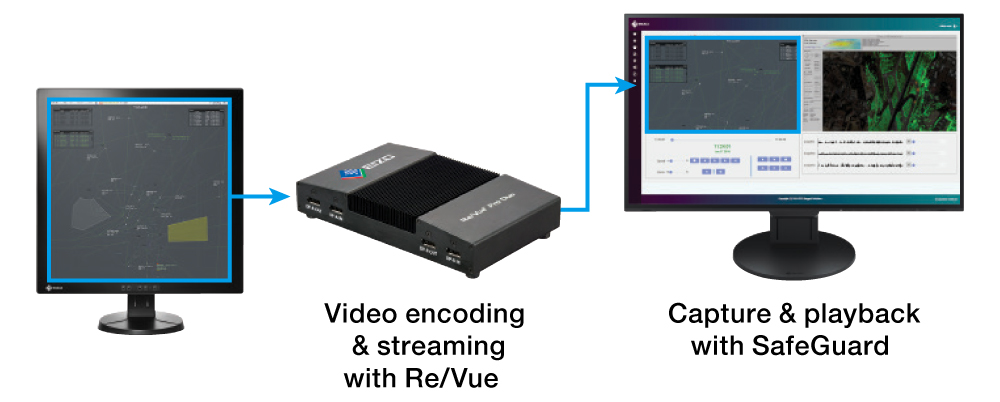
An example of such a product is EIZO’s Re/Vue line of video encoding and streaming solutions. It uses EIZO’s propriety compression algorithm, designed to provide lossless encoding of video data at full frame rate up to and including 8MP displays, with reduced bandwidth and storage requirements. As the data is transferred over the network from encoder to capture server, its proprietary nature ensures that any attempt to interrogate and intercept the data would be futile. This is especially useful in systems whereby capture is not localized and uses a WAN for transfer. At the same time, vendor lock-in is avoided by providing decoding and export tools to privileged administrators. These tools allow archived data to be converted to standard formats only under the most secure conditions. |
Re/Vue products used together with SafeGuard provide a highly secure archive for data management, analysis, and distribution. |
Conclusion
By combining IT system and physical security features, considering the implications of network security and providing a flexible yet secure data access methodology, in addition to a data storage architecture that guarantees almost 100% availability, ANSPs can be safe in the knowledge that they will be provided with a secure environment to address their data capture and retention needs.
As greater reliance is placed on the storage of data outside the center in which it is captured, the transfer of data and its security during and after the process will change. EIZO’s SafeGuard solution was developed with this migration in mind and is designed to handle the issues associated with the remote storage and access of captured data. It has been designed from the ground up with a clear understanding of the issues that are faced as technology continues to develop in ATM systems and by anticipating future market requirements. By addressing the issues associated with security and accessibility from the outset, and also considering the needs of the wide range of users involved, SafeGuard can be customized in line with customer requirements.
Recommended Products
 |
 |
 |
 |
|
Integrated Data Capture & |
Dual-Channel Encoding & Streaming Solution |
 |
 |